Azure Virtual Machine Tutorial
The Crazy Programmer
JULY 25, 2020
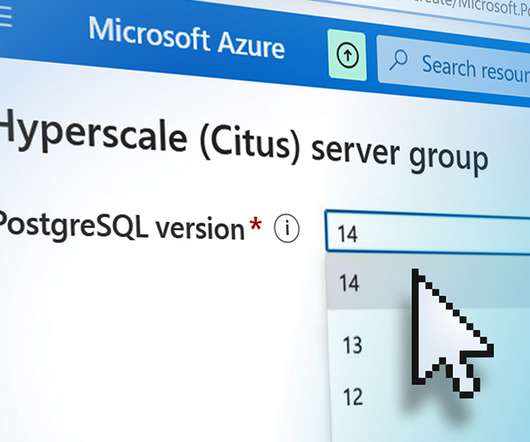
OS guest diagnostics – You can turn this on to get the metrics per minute. Diagnostics storage account – It is a storage account where your metrics will be written so we can also analyze them with other tools if we want. It helps to solve the startup issues. For more – [link]. I recommended you to turn this on.







































Let's personalize your content