CrowdStrike incident has CIOs rethinking their cloud strategies
CIO
JULY 22, 2024
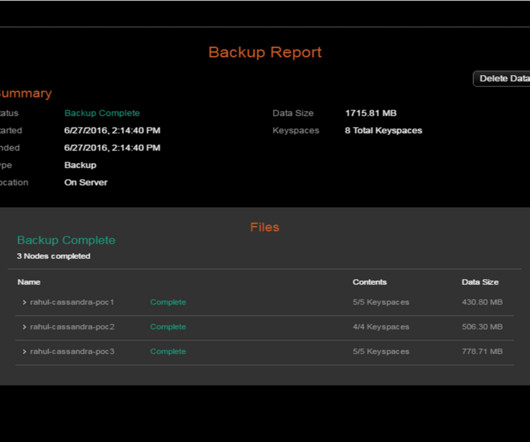
The widespread disruption caused by the recent CrowdStrike software glitch, which led to a global outage of Windows systems, has sent shockwaves through the IT community. For CIOs, the event serves as a stark reminder of the inherent risks associated with over-reliance on a single vendor, particularly in the cloud.
















































Let's personalize your content