Three Reasons Endpoint Security Can’t Stop With Just Patching
Ivanti
JUNE 14, 2023
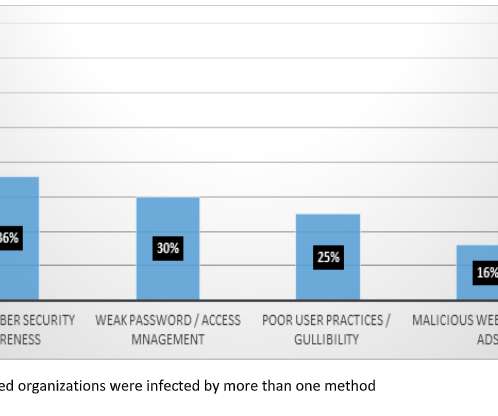
AI generated polymorphic exploits can bypass leading security tools Recently, AI-generated polymorphic malware has been developed to bypass EDR and antivirus, leaving security teams with blind spots into threats and vulnerabilities. This mutation is not detectable by traditional signature-based and low-level heuristics detection engines.
































Let's personalize your content