What is Incident Response?
xmatters
JULY 2, 2024
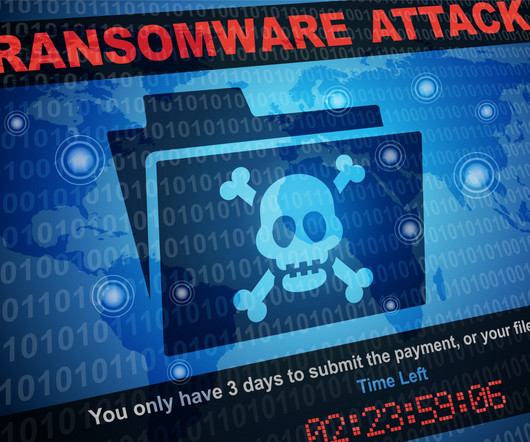
Malware Malware is malicious software designed to harm, exploit, or otherwise compromise a computer system or network. During this phase, the organization also updates malware protection, patches vulnerabilities, and reconfigures security settings as needed. Request a demo The post What is Incident Response?





































Let's personalize your content