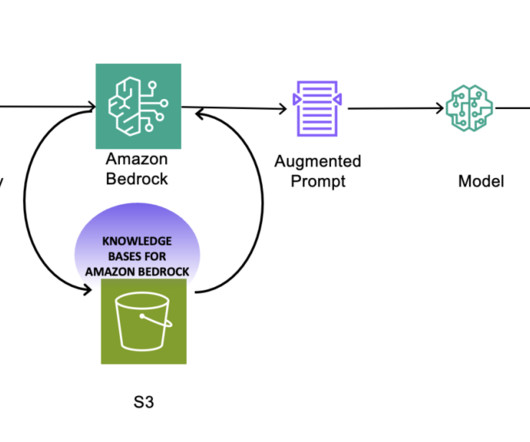
Implementing Knowledge Bases for Amazon Bedrock in support of GDPR (right to be forgotten) requests
AWS Machine Learning - AI
MAY 31, 2024
This streamlined approach simplifies the GDPR right to be forgotten compliance for generative AI applications. Audit tracking To support GDPR compliance efforts, organizations should consider implementing an audit control framework to record right to be forgotten requests. However, this is beyond the scope of this post.






















Let's personalize your content