Architect defense-in-depth security for generative AI applications using the OWASP Top 10 for LLMs
AWS Machine Learning - AI
JANUARY 26, 2024
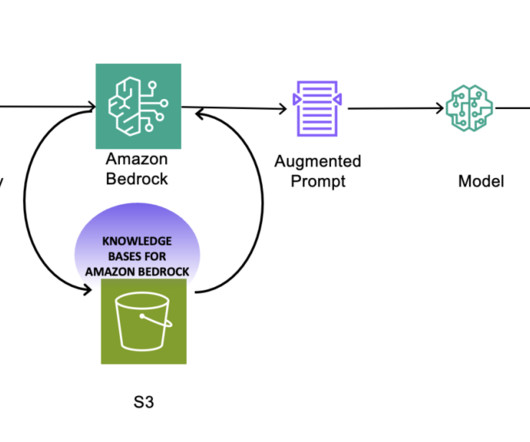
Many customers are looking for guidance on how to manage security, privacy, and compliance as they develop generative AI applications. What operational and technical best practices can I integrate into how my organization builds generative AI LLM applications to manage risk and increase confidence in generative AI applications using LLMs?
.jpg)
















Let's personalize your content