Create your Private Data Warehousing Environment Using Azure Kubernetes Service
Cloudera
DECEMBER 2, 2021
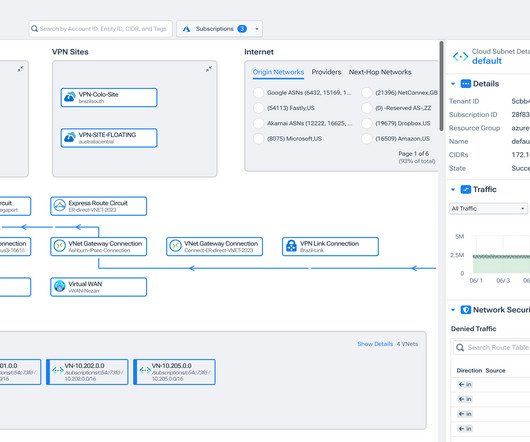
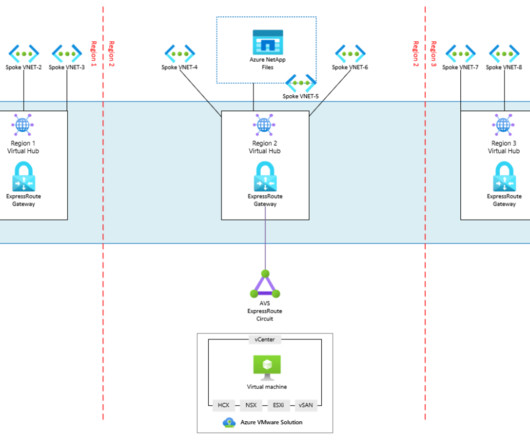
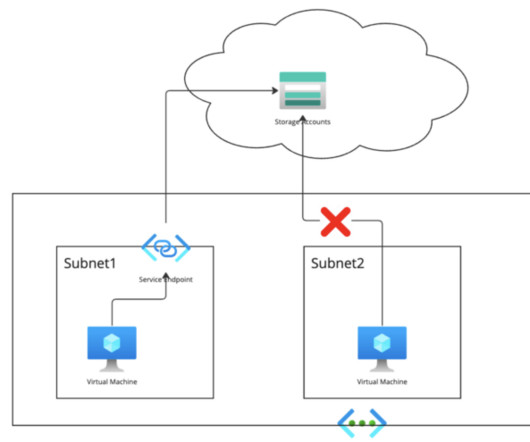
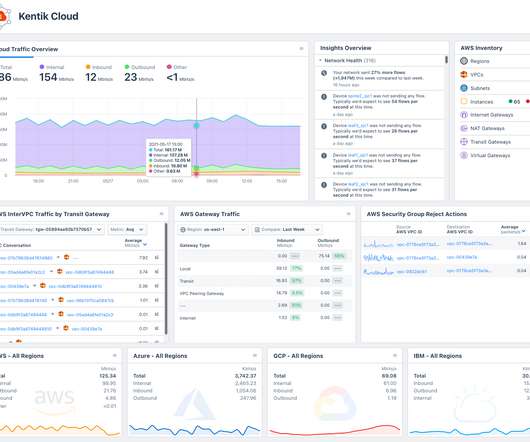
It is part of the Cloudera Data Platform, or CDP , which runs on Azure and AWS, as well as in the private cloud. This post explains how CDW helps you maximize the security of your cloud data warehousing platform when running in Azure. . As such, it is now possible to run a private CDW environment in Azure. Network Security.
























Let's personalize your content