Ex-Plaid employees raise $30M for Stytch, an API-first passwordless authentication platform
TechCrunch
JULY 14, 2021
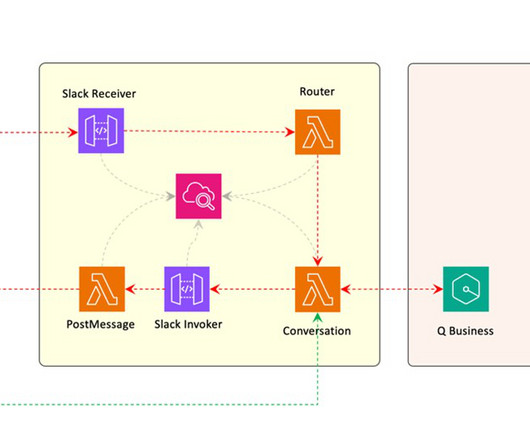
One such company, Stytch , just raised $30 million in a Series A round of funding as it launches out of beta with its API-first passwordless authentication platform. Lamb says that as she and McGinley-Stempel worked together at Plaid on user authentication, they realized how frustrating it is to build sign-up and login flows. “In
















































Let's personalize your content