Accelerate AWS Well-Architected reviews with Generative AI
AWS Machine Learning - AI
MARCH 4, 2025
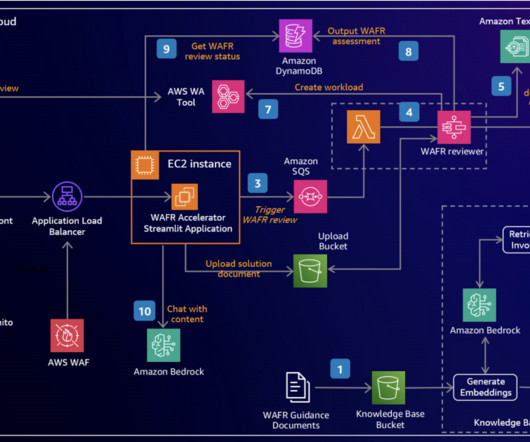
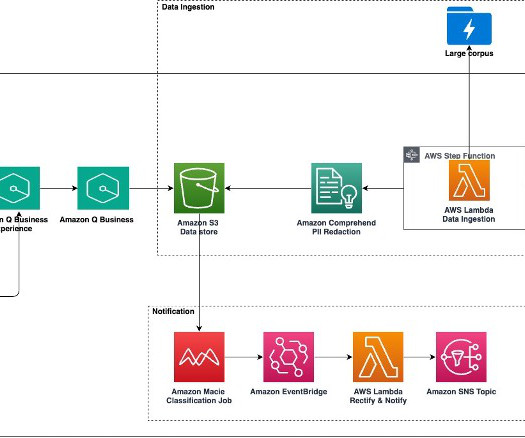
As systems scale, conducting thorough AWS Well-Architected Framework Reviews (WAFRs) becomes even more crucial, offering deeper insights and strategic value to help organizations optimize their growing cloud environments. In this post, we explore a generative AI solution leveraging Amazon Bedrock to streamline the WAFR process.














































Let's personalize your content