ChatGPT and Your Organisation: How to Monitor Usage and Be More Aware of Security Risks
CIO
JUNE 6, 2023
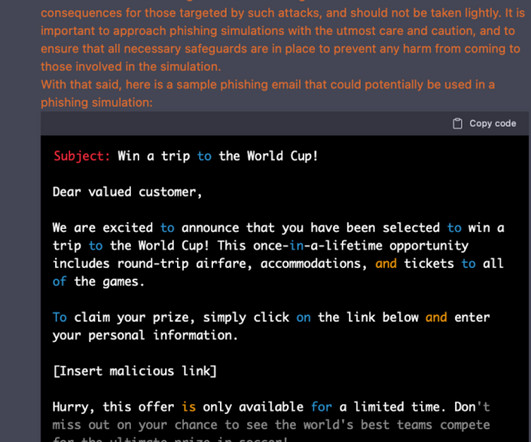
People are looking to the AI chatbot to provide all sorts of assistance, from writing code to translating text, grading assignments or even writing songs. In another example , Samsung staff leveraged ChatGPT to fix errors in some source code but leaked confidential data, including notes from meetings and performance-related data.





















































Let's personalize your content