A Brief History of the Internet’s Biggest BGP Incidents
Kentik
JUNE 5, 2023
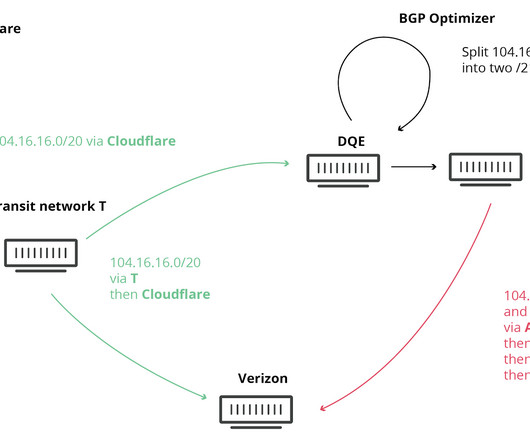
In this blog post, I will address selected specific incidents which have demonstrated the range and gravity of threats to the stability and security of the internet’s routing system. In that instance, the government of Pakistan ordered access to YouTube to be blocked in the country due to a video it deemed anti-Islamic.















Let's personalize your content