Truepic, which just raised $26M in a Microsoft-led round, aims to verify the authenticity of photos and videos
TechCrunch
SEPTEMBER 14, 2021
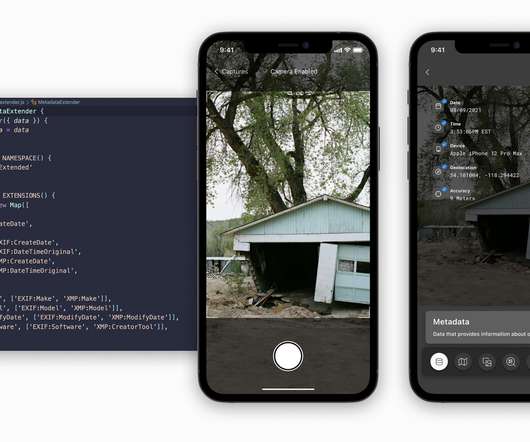
As such, the company says its software can authenticate where photos were taken and prove that they were not manipulated since there are an increasing number of deceptive photos and personal information that can be purchased on the Dark Web, social media and via software that can change the metadata of an image’s time or location. “Our















































Let's personalize your content