Solving the tech debt problem while staying competitive and secure
CIO
AUGUST 1, 2024
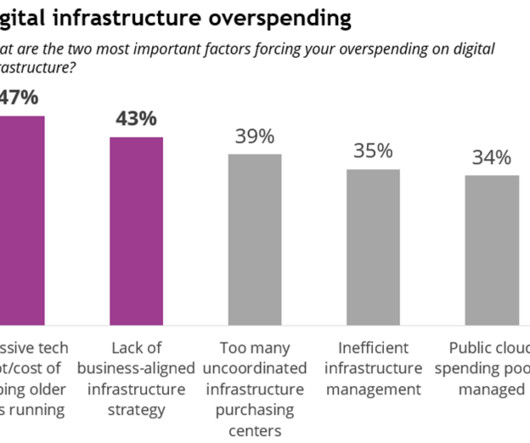
Looking ahead to the next 12-18 months, two top priorities emerge for IT leaders: developing a strong business case for AI infrastructure spending (cited by 35% of respondents to IDC’s Future Enterprise Resiliency and Spending Survey, Wave 3 , March 2024) and increasing cyber resilience and security (34%).














































Let's personalize your content