Build and deploy a UI for your generative AI applications with AWS and Python
AWS Machine Learning - AI
NOVEMBER 6, 2024
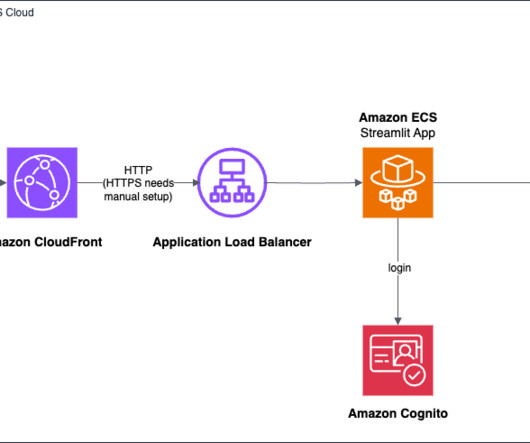
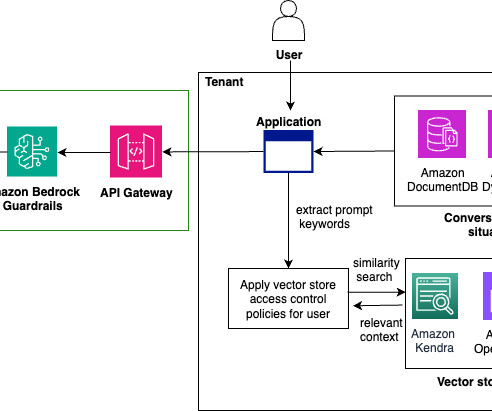
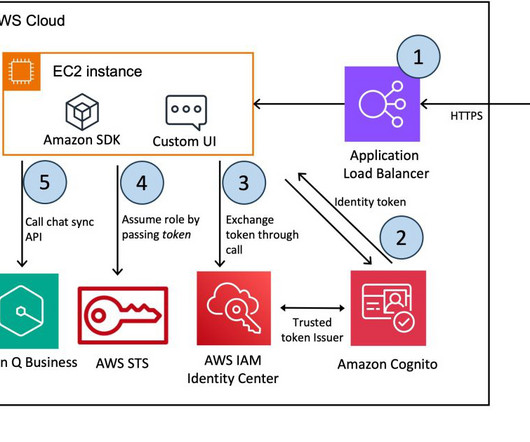
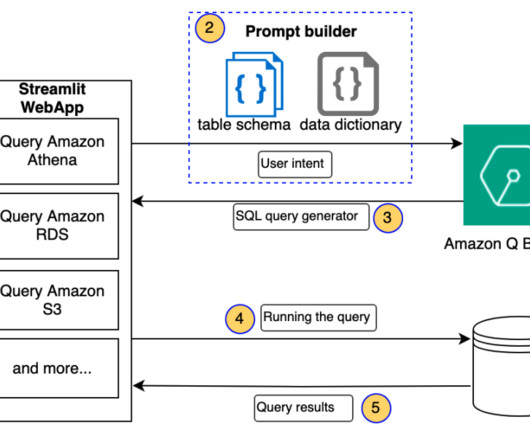
The emergence of generative AI has ushered in a new era of possibilities, enabling the creation of human-like text, images, code, and more. The AWS deployment architecture makes sure the Python application is hosted and accessible from the internet to authenticated users. The AWS Command Line Interface (AWS CLI).












































Let's personalize your content