Operate Efficiently and Securely: Rotating Prisma Cloud Access Keys
Prisma Clud
MAY 21, 2024
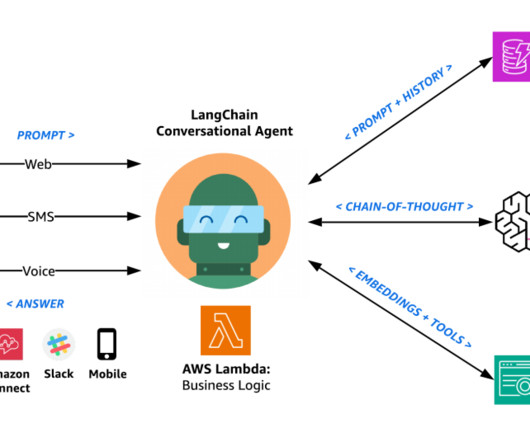
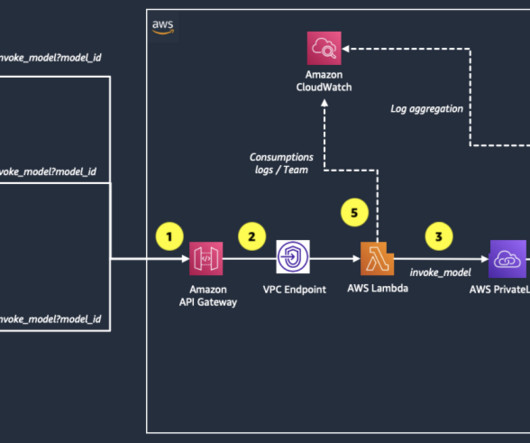
Ensuring appropriate access management is a critical component of any effective cloud security strategy. Prisma Cloud Access Keys are a secure way to enable programmatic access to the Prisma Cloud API, if you are setting up an external integration or automation. Take this real-world scenario, for example. Instead, they use access keys.














































Let's personalize your content