Otterize raises $11.5M to help developers securely connect software services
TechCrunch
APRIL 13, 2023
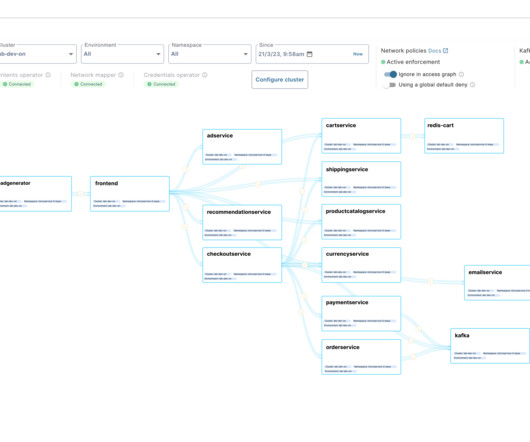
Tomer Greenwald, Uri Sarid and Ori Shoshan, software developers by trade, found themselves building and configuring software authentication and authorization mechanisms repeatedly — each time with a different tech stack. Otterize today raised $11.5 Otterize today raised $11.5


















































Let's personalize your content