How Druva used Amazon Bedrock to address foundation model complexity when building Dru, Druva’s backup AI copilot
AWS Machine Learning - AI
NOVEMBER 1, 2024
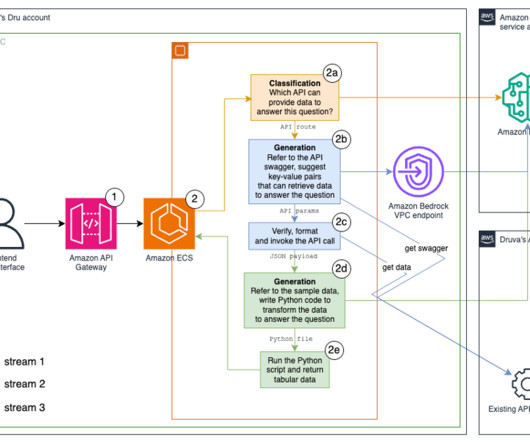
Dru , the Druva backup AI copilot, enables real-time interaction and personalized responses, with users engaging in a natural conversation with the software. From finding inconsistencies and errors across the environment to scheduling backup jobs and setting retention policies, users need only ask and Dru responds.

















































Let's personalize your content