Make a resolution to clean up your digital act? Here’s how
The Parallax
DECEMBER 28, 2017
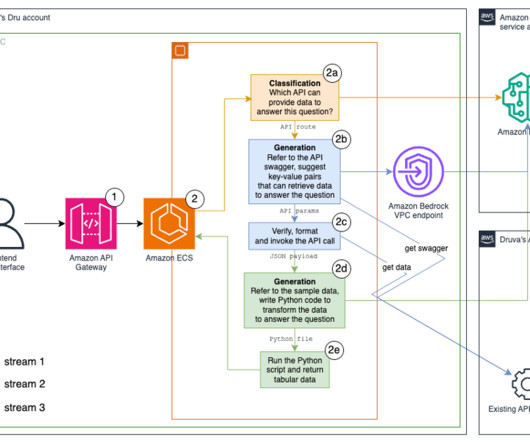
Step 1: Use two-factor authentication. In its most common form online, two-factor authentication makes you use a second, one-time password to access your account. Set up your phone with a passcode or other security measure, use two-factor authentication (there it is again!), and use only apps that have been verified as safe.

















































Let's personalize your content