Using natural language in Amazon Q Business: From searching and creating ServiceNow incidents and knowledge articles to generating insights
AWS Machine Learning - AI
DECEMBER 18, 2024
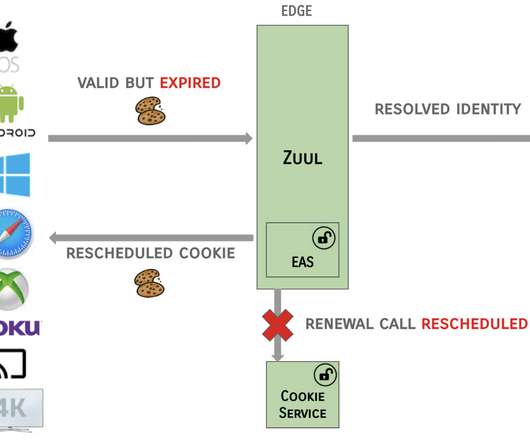
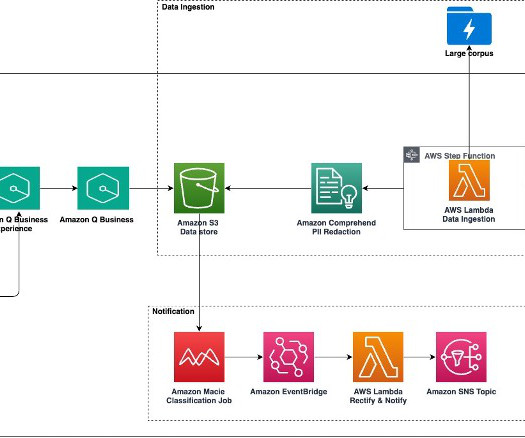
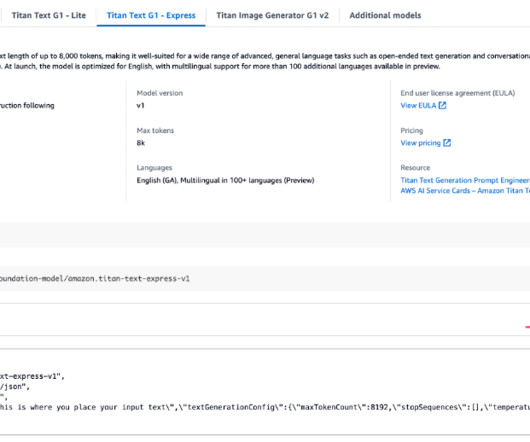
Generative AIpowered assistants such as Amazon Q Business can be configured to answer questions, provide summaries, generate content, and securely complete tasks based on data and information in your enterprise systems. For more information, see OAuth Inbound and Outbound authentication.

















































Let's personalize your content