The Case for Software Architecture Makeover
Dzone - DevOps
JUNE 22, 2021
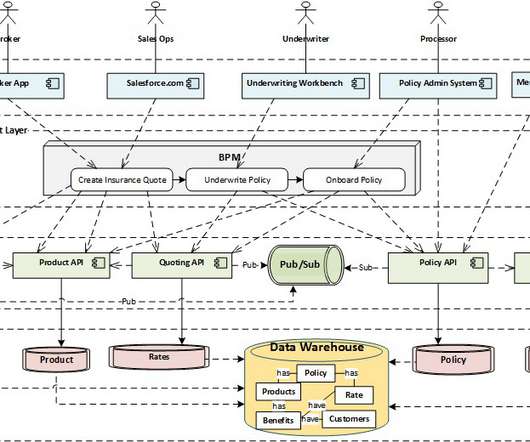
A few years ago, a friend of mine shared with me a white paper that he thought would interest me. This paper described the concept of distributed application architecture through small self-contained application components deployed across a larger corporate network. He smiled and replied, “Look at the published date.”

















































Let's personalize your content