Agentic AI design: An architectural case study
CIO
NOVEMBER 19, 2024
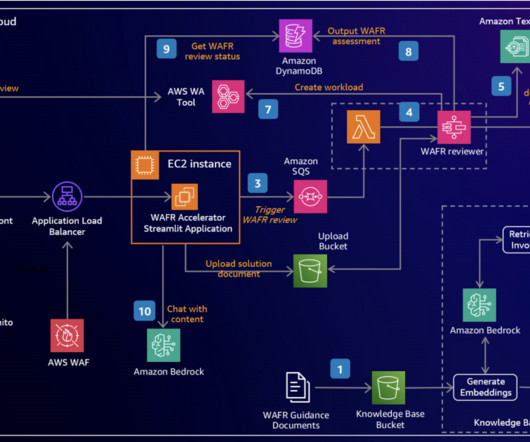
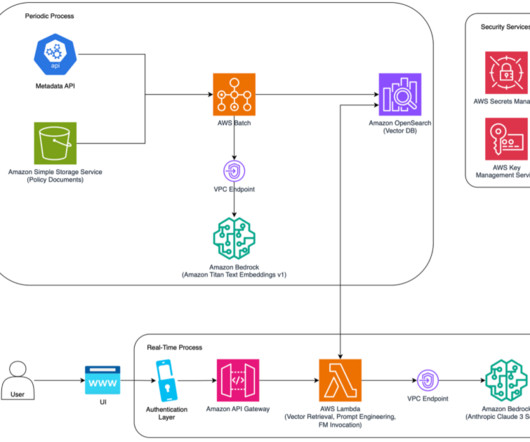
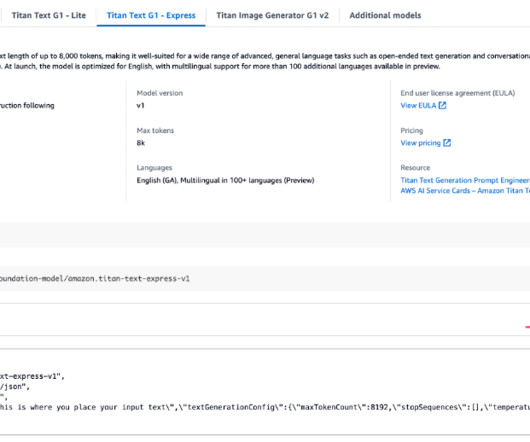
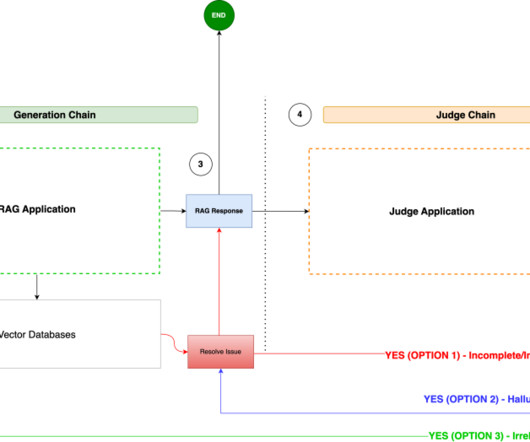
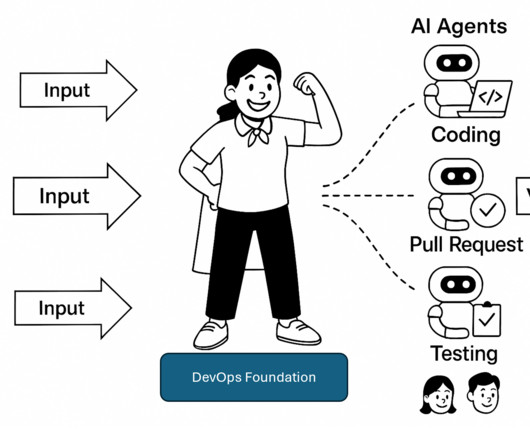
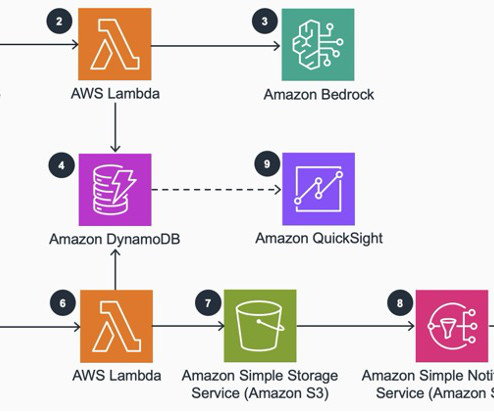
Agentic AI is the next leap forward beyond traditional AI to systems that are capable of handling complex, multi-step activities utilizing components called agents. He believes these agentic systems will make that possible, and he thinks 2025 will be the year that agentic systems finally hit the mainstream. They have no goal.











































Let's personalize your content