Agile Book Club: System Architecture
James Shore
JULY 6, 2022
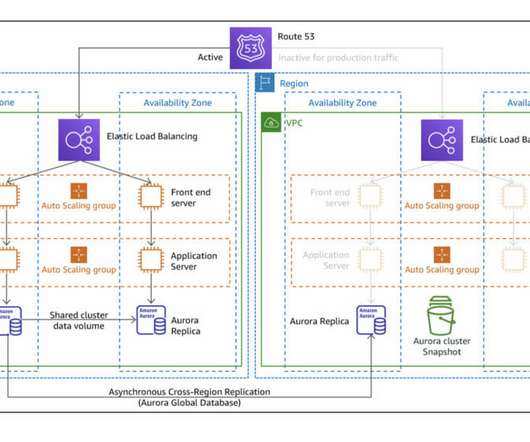
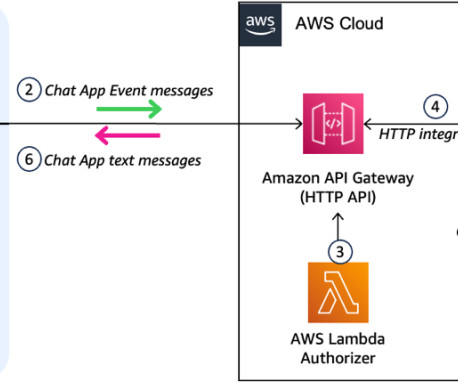
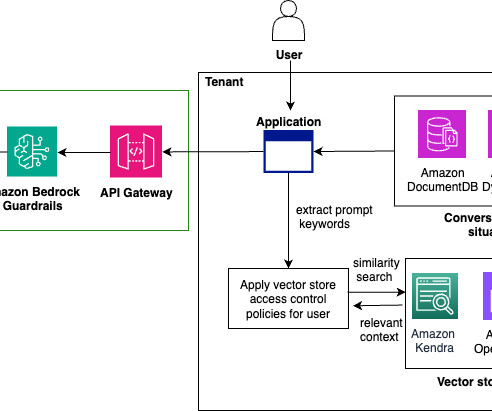
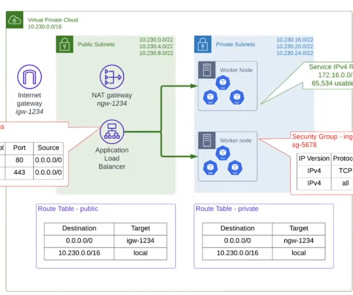
Applications and services, network gateways and load balancers, and even third-party services? Those components and interactions form your system architecture. Evolutionary System Architecture. ?? Discussion prompts: How have you seen teams approach designing system architecture? Reading: ?? About the Book Club.












































Let's personalize your content