Why “café-like branches” are the latest buzz among CIOs
CIO
MARCH 5, 2025
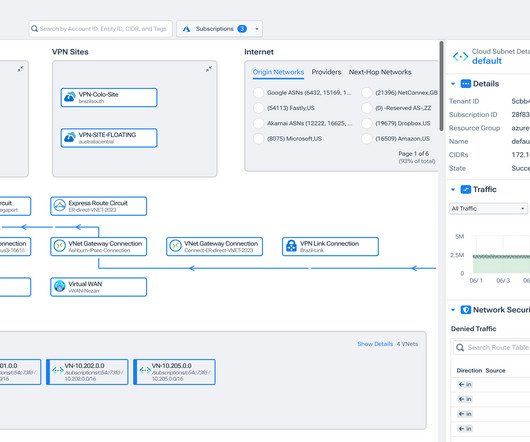
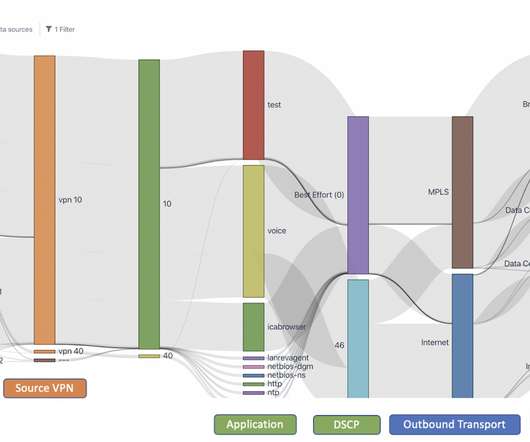
To answer this, we need to look at the major shifts reshaping the workplace and the network architectures that support it. The Foundation of the Caf-Like Branch: Zero-Trust Architecture At the heart of the caf-like branch is a technological evolution thats been years in the makingzero-trust security architecture.


















































Let's personalize your content