Bridging the gap: Unified platform for VM and containerized workloads
CIO
NOVEMBER 4, 2024
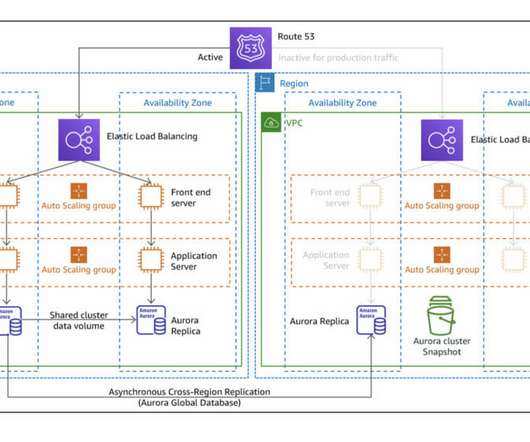
To keep up, IT must be able to rapidly design and deliver application architectures that not only meet the business needs of the company but also meet data recovery and compliance mandates. Moving applications between data center, edge, and cloud environments is no simple task.


















































Let's personalize your content