Serverless, it can help you brew beer
Xebia
OCTOBER 25, 2024
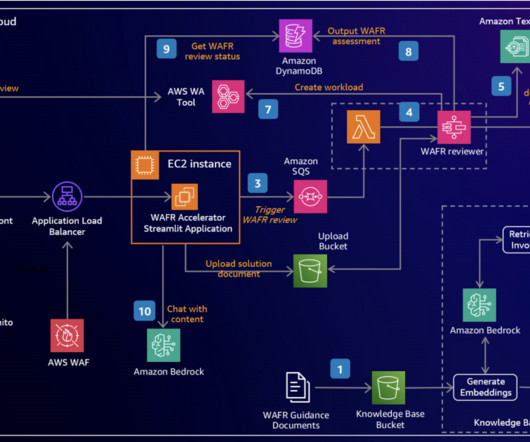
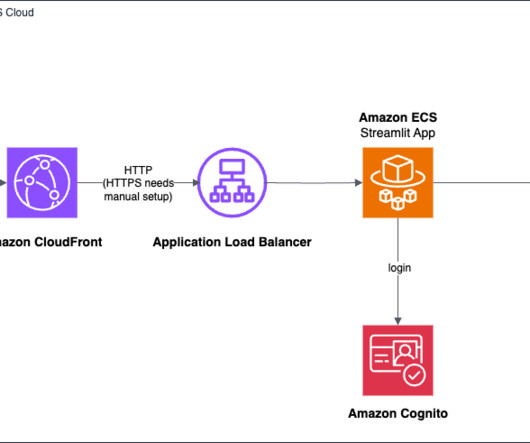
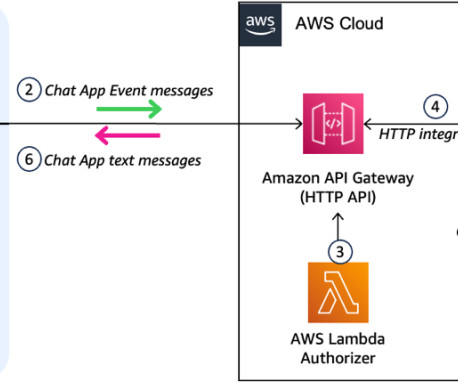
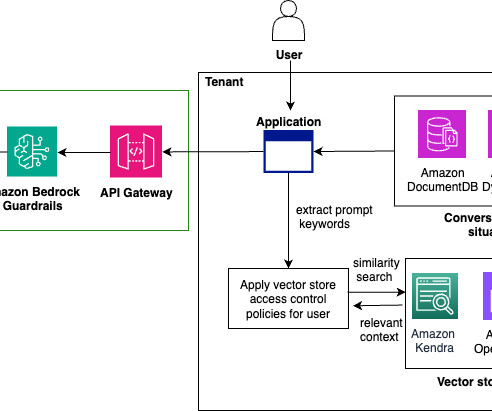
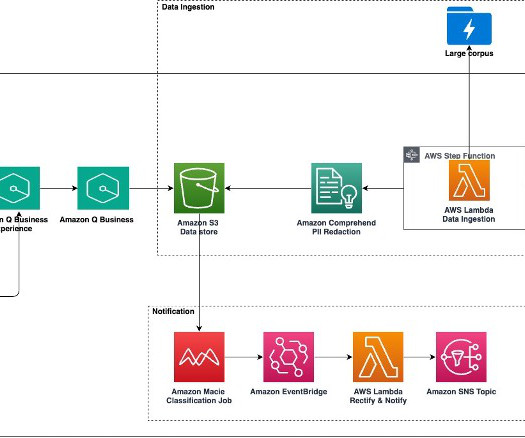
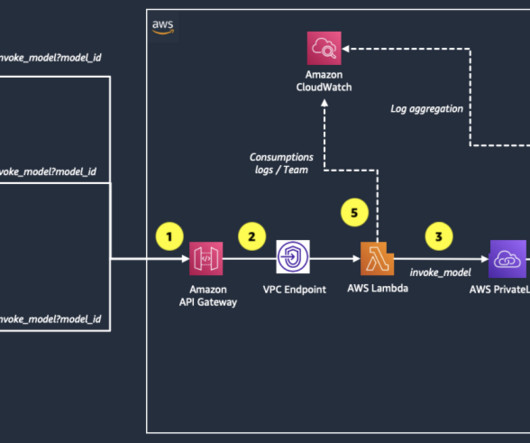
How does Serverless help? The documentation clearly states that you should not use the usage plans for authentication. Conclusion Real-world examples help illustrate our options for serverless technology. Based on those questions, you might pivot your solution’s architecture. It’s slowly changing from wort to beer.











































Let's personalize your content