React authentication, simplified
David Walsh
MARCH 4, 2021
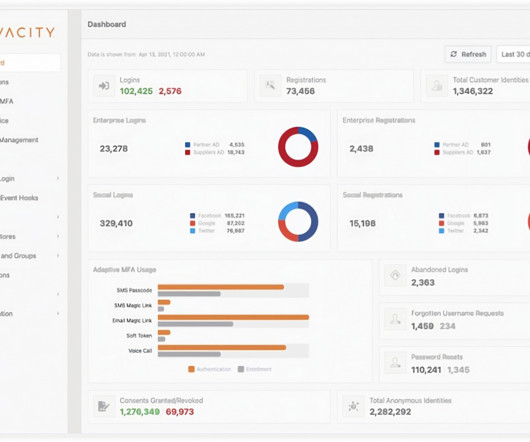
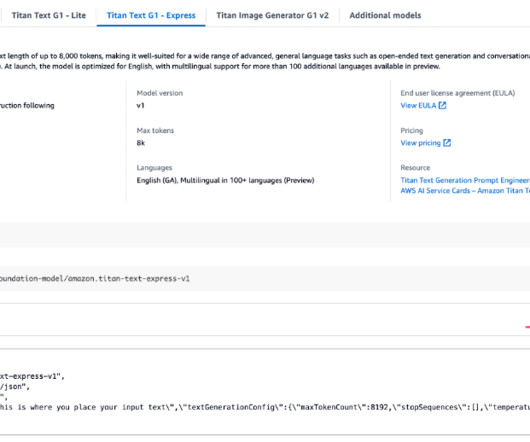
Authentication is one of those things that just always seems to take a lot more effort than we want it to. To set up auth, you have to re-research topics you haven’t thought about since the last time you did authentication, and the fast-paced nature of the space means things have often changed in the meantime. React authentication.











































Let's personalize your content