Unit 42 Discovers First Known Malware Targeting Windows Containers
Palo Alto Networks
JUNE 7, 2021
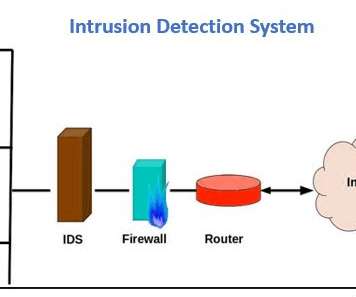
The Unit 42 cybersecurity consulting group published research on the first known malware targeting Windows containers, which was discovered by Unit 42 researcher Daniel Prizmant and named Siloscape. Containers provide an easy way to run applications in the cloud. In addition to containers, there are clusters.



















































Let's personalize your content