NeuraLight aims to track ALS, Parkinson’s and more with an ordinary webcam
TechCrunch
MAY 24, 2022
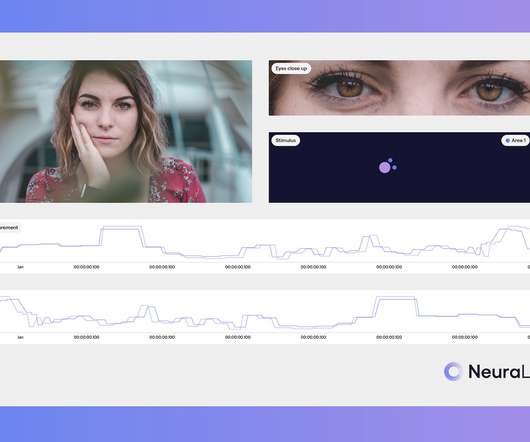
This confidence crisis in the data needs an objective metric to be mitigated, and that’s what NeuraLight, based in Austin and Tel Aviv, is building. This, along with other eye movements and metrics, has been linked to neurological disorders for years in numerous publications. ” Image Credits: NeuraLight.















































Let's personalize your content