Top 10 Highest Paid Programming Languages in 2019
The Crazy Programmer
JULY 8, 2019
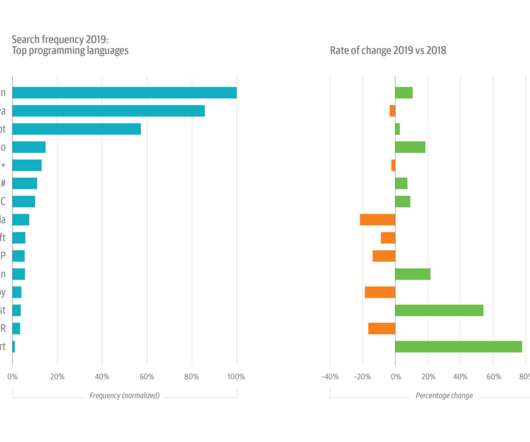
This data is according to the Stack Overflow Developer Survey 2019. 10 Highest Paid Programming Languages in 2019. This language can fetch the developers a salary much closer to around six-figure due to the dependency of Apple on this language. So, here is the list of a top paying programming languages in the market.


























Let's personalize your content