Case in point: taking stock of the CrowdStrike outages
CIO
APRIL 2, 2025
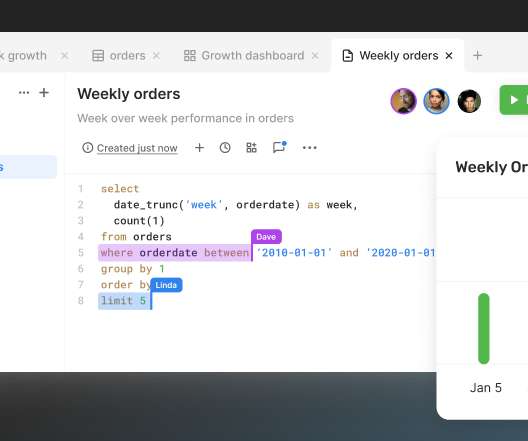
What happened In CrowdStrikes own root cause analysis, the cybersecurity companys Falcon system deploys a sensor to user machines to monitor potential dangers. By comparison, the previous record-holder for most expensive downtime was the 2017 AWS outage, which cost customers an estimated $150 million. Clancy asks. Trust, but verify.










































Let's personalize your content