QA Wolf exits stealth with an end-to-end service for software testing
TechCrunch
SEPTEMBER 7, 2022
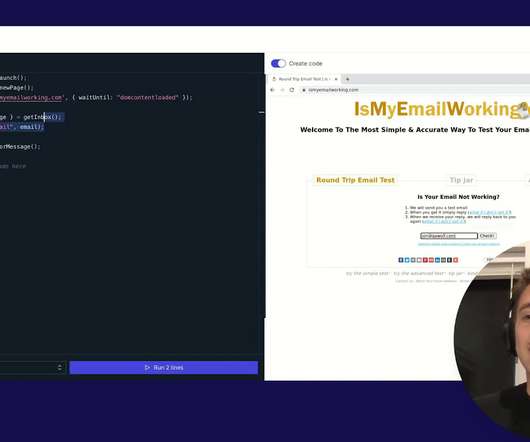
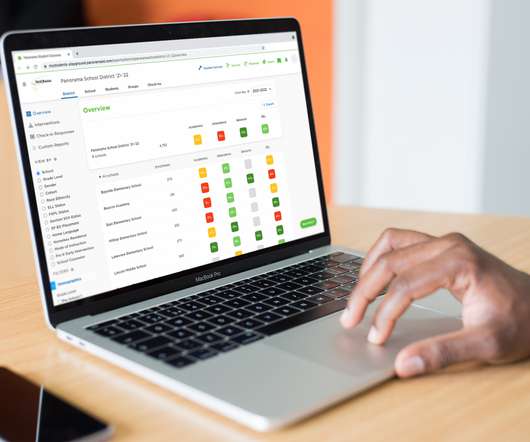
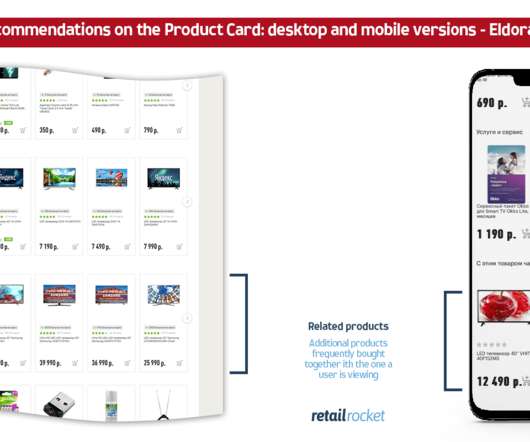
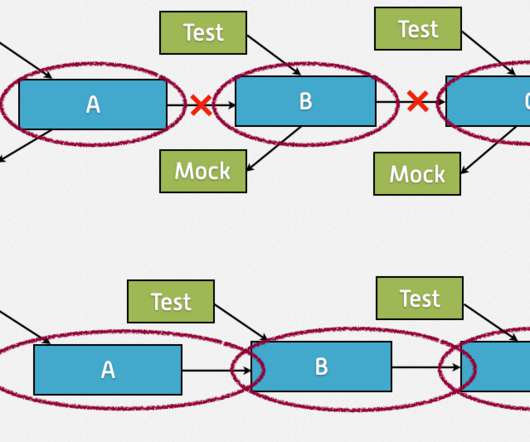
QA Wolf , a cloud-based platform designed to detect bugs in software, today exited stealth and announced a $20 million funding round led by Inspired Capital with participation from Notation Capital, Operator Partners and Thiel Capital and several angel investors (among them Peter Thiel). Neither, obviously, are very desirable scenarios.















































Let's personalize your content