Cloud Security — Maturing Past the Awkward Teenage Years
Palo Alto Networks
OCTOBER 22, 2024
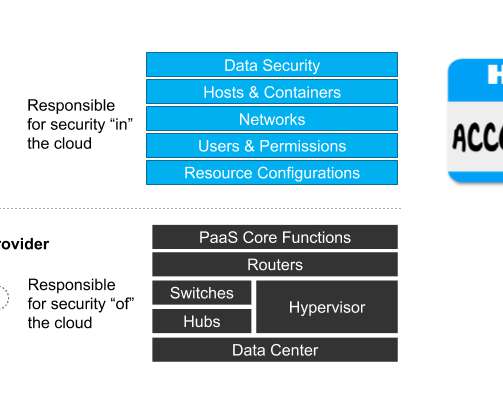
{{interview_audio_title}} 00:00 00:00 Volume Slider 10s 10s 10s 10s Seek Slider The genesis of cloud computing can be traced back to the 1960s concept of utility computing, but it came into its own with the launch of Amazon Web Services (AWS) in 2006. This alarming upward trend highlights the urgent need for robust cloud security measures.




























Let's personalize your content