How Wi-Fi router security has deteriorated since 2003
The Parallax
JANUARY 24, 2019
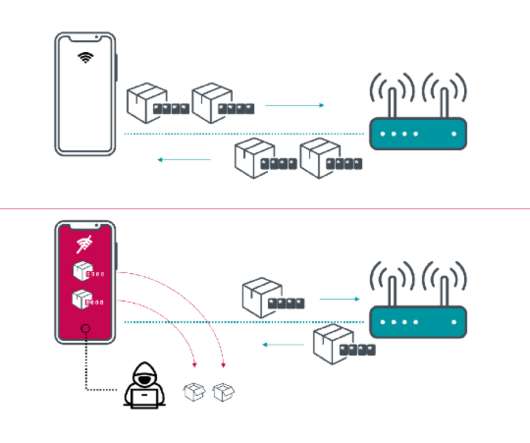
The Cyber Independent Testing Lab , a nonprofit organization that focuses on consumer cybersecurity, published research in December demonstrating how 28 home wireless routers fail to use even basic security techniques. D-Link takes the issues of network security and user privacy very seriously.”. READ MORE ON WI-FI SECURITY.















































Let's personalize your content