Tetrate, the company born out of Istio’s open-source app networking project, raises $40 million
TechCrunch
MARCH 10, 2021
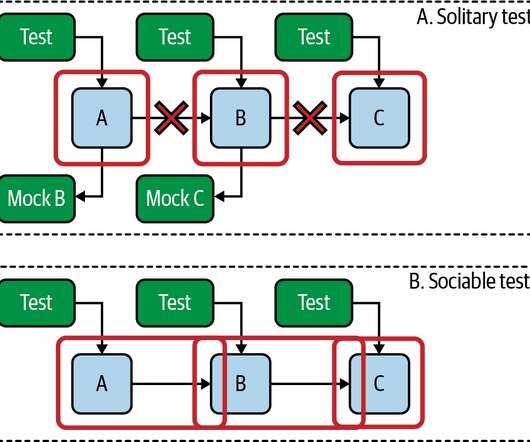
As the microservices revolution picks up steam, it’s indispensable to use Istio for managing applications built with microservices and deployed on containers. Tetrate nets $12.5 million to bring microservices to the corporate masses. “We Container security acquisitions increase as companies accelerate shift to cloud. “As





































Let's personalize your content